If you’re in banking, you know the drill. Adhering to stringent EU regulations is a standard practice. This involves undergoing extensive audits, closely managing IT assets, maintaining your CIA (Confidentiality, Integrity, Availability) rating, conducting and responding to fire drills, and establishing continuity plans. So far, nothing new, and if you’re in other highly regulated environments, you know that these measures are commonplace.
As an IT manager at ING, one of the larger banks in the Netherlands, these tasks were part of my daily routine. It was very clear to me that maintaining control was super important. Everything I did had a primary focus: managing IT risk.
With the Digital Operational Resilience Act (DORA) on the horizon, there's a sudden surge in attention towards IT risk management. This has implications across different levels within organizations:
For engineering managers, this means ensuring adherence to best practices in software development and system architecture to bolster operational resilience.
Senior decision-makers will have to allocate resources and prioritize initiatives that support DORA compliance.
IT teams are responsible for implementing measures to achieve DORA compliance.
All of this is to say, "It's time to get ready to be DORA Compliant."
As the financial industry prepares for the significant regulatory change brought by DORA, the importance of comprehensive IT risk management has never been clearer. In this landscape of stringent audits and complex compliance demands, StackState can help out by offering an observability platform that transcends traditional IT monitoring.
This blog article examines how StackState prepares organizations for DORA compliance and revolutionizes their perception and management of IT risks, ensuring that resilience and efficiency become the cornerstones of their digital infrastructure.
Introducing Digital Operational Resilience Act (DORA)
With the arrival of DORA in 2025, Information and Communications Technology (ICT) Risk will take center stage. You might be wondering if your company is prepared to deal with DORA or, more importantly, what steps need to be taken to ensure readiness. Compliance with the new EU Regulation 2022/2554 may be a top priority.
Let's explore a specific part of the new DORA regulation and highlight how StackState can assist. Sections 2, chapters 6 to 16 are particularly relevant.
We’ll aim our focus on how ICT Risk Management is shaped within the following five topics:
Identification
Protection and Prevention
Detection
Response and Recovery
Learning and Evolving
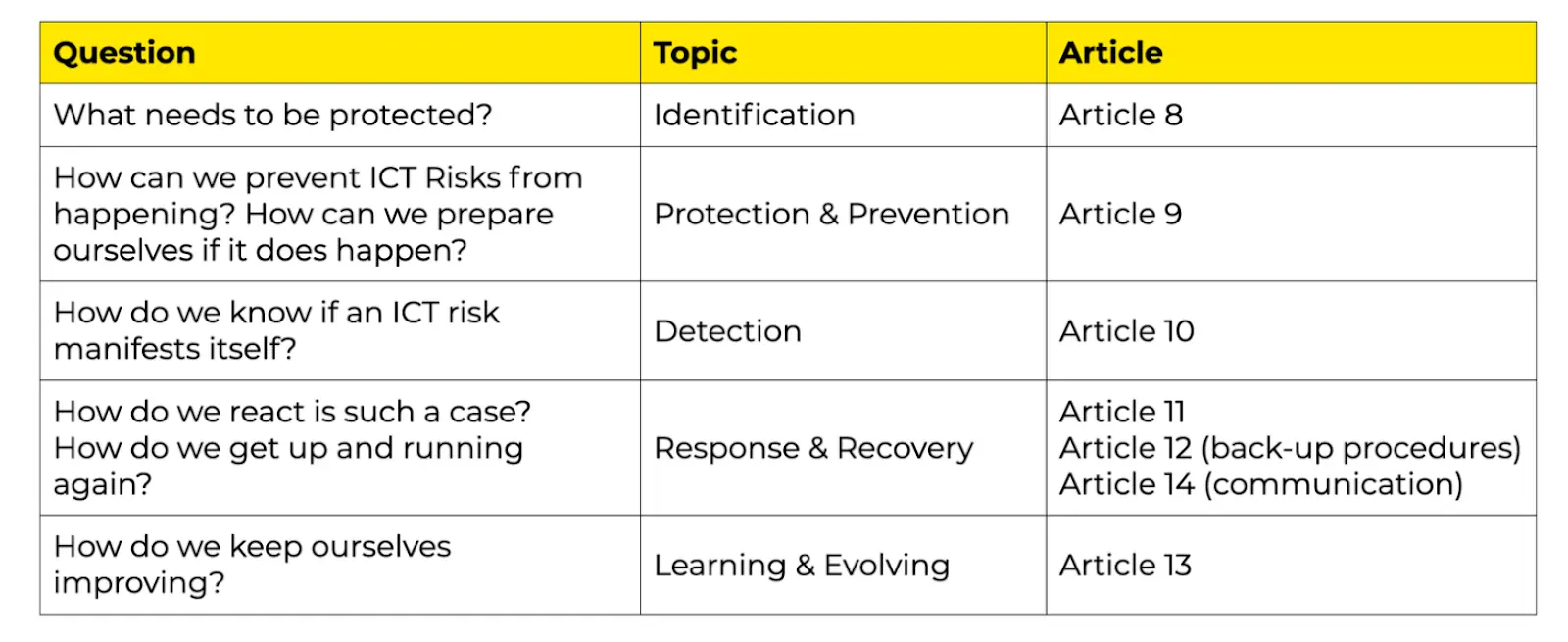
Let's avoid the theoretical framework and break down the topics above into actionable steps, helping you understand what it means to apply them in practice.
Topic 1: Identification
For IT managers navigating DORA's requirements, the key focus of the 'identification' section is the thorough documentation and classification of all IT-supported business functions, information, and ICT assets, including their roles and interdependencies.
This involves continuous assessment of ICT risks, regular reviews, and updating records after significant infrastructural changes. Mapping and inventory maintenance of all ICT assets is super important, as is the documentation of processes reliant on third-party ICT services.
This rigorous identification and documentation process helps create a strong foundation for managing and mitigating ICT risks, which aligns with DORA's objective of boosting the resilience of financial organizations. While tools like CMDB can be helpful for tracking inventory, in my experience as an IT manager, it's difficult to keep them completely up-to-date and aligned with what's really happening.
Topic 2: Protection and Prevention
To meet DORA's ‘protection and prevention’ requirements, financial entities need to consistently monitor and control their ICT systems for security and availability. This includes implementing suitable security and monitoring tools, as well as policies and procedures, to minimize the impact of ICT risks from the start.
Financial entities will need to develop and put into action ICT security policies focused on resilience and data protection. These policies should address aspects like data transfer, minimizing data loss or corruption, ensuring data availability, and protecting against management risks. Key components of the policy should include access control, robust authentication methods, encryption, change management, and patch management.
In addition, we have to emphasize the significance of system availability and ongoing monitoring. These elements are essential for maintaining operational resilience and guaranteeing that financial services remain uninterrupted. You'll find that effective observability enables early detection of possible security issues while prioritizing system availability ensures continuous access to critical financial processes, which in turn protects the operational integrity of the institution.
Topic 3: Detection
For IT managers in financial entities, DORA's emphasis on ‘detection’ involves establishing strong mechanisms to quickly identify unusual activities, such as network performance problems and ICT-related incidents.
This includes establishing multiple layers of control, defining alert thresholds, and initiating incident response procedures. It also entails allocating adequate resources to monitor user activity and ICT anomalies, particularly cyber-attacks.
Effective detection is key to preemptively identifying potential failures and safeguarding the resilience and security of financial systems. This approach aligns with observability practices, facilitating a more responsive and proactive IT environment.
Topic 4: Response & Recovery
For IT managers, DORA's sections on ‘response and recovery’ underscore the significance of having a thorough ICT business continuity policy in place. This policy should undergo regular testing and updates, particularly following noteworthy changes in ICT systems. It involves creating detailed response and recovery plans, performing business impact analysis, and upholding crisis communication protocols.
This guarantees not just the quick resolution of ICT-related incidents but also ensures that ICT systems align with the broader business continuity strategy. The aim is to minimize disruptions to critical functions while continuing to provide seamless operations.
Topic 5: Learning and Evolving
The ‘learning and evolving’ section of DORA stresses the importance of continuous improvement in digital operational resilience. Financial organizations are tasked with gathering and analyzing data on vulnerabilities, cyber threats, and ICT-related incidents to bolster their resilience. However, real progress occurs during post-incident reviews, where disruptions are evaluated, and ICT operations are refined.
Regular monitoring and updating of the digital operational resilience strategy are just as important as staying informed about technological advancements. Training programs in ICT security and resilience should be mandated for all staff, including senior management, to establish a proactive and informed approach to managing ICT risks.
How StackState supports enterprises navigating DORA
StackState can be incredibly helpful in numerous aspects of this IT risk framework. By providing the tools and insights needed for every stage of compliance and resilience building, our full-stack observability platform aims to meet — and exceed — the requirements outlined by DORA. Here’s how:
Identification — By utilizing StackState's automated process for monitoring, correlating, and analyzing topology changes and metrics, businesses can establish a strong foundation for understanding all IT assets — and their relationships — within their environment. This includes understanding when components are added or removed.
Protection and Prevention — StackState’s out-of-the-box observability brings all your business apps together in a single view and provides continuous data correlation to help you proactively safeguard the end-user experience. By offering a comprehensive 360-degree view of your entire mission-critical infrastructure, it fosters cross-team collaboration and drives innovation.
Detection — By capturing and displaying real-time data alongside historical data, our dynamic topology facilitates quicker issue identification and better troubleshooting. Coupled with our state-of-the-art dependency maps, which plot all interdependency changes over time, StackState’s end-to-end observability platform alerts your engineers to issues as they occur. This allows them to easily diagnose the root cause for faster and more thorough resolution.
Response and Recovery — StackState's abilities in event correlation, topology intelligence, and time-travel insights facilitate the development of comprehensive ICT business continuity policies backed by detailed 'response and recovery' plans, business impact analysis, and the upkeep of crisis communication protocols. Additionally, StackState offers remediation guides to assist engineering teams in quickly troubleshooting and resolving detected issues.
Learning and Evolving — StackState fosters continuous improvement in digital operational resilience. After issues are detected, resolved, and thoroughly analyzed through a postmortem process, the insights gained can flow back into new or adjusted policies and remediation guides. These efforts aim to prevent similar issues in the future and expedite remediation if they do recur.
Rest assured, with StackState, you're ready for DORA
In an era where digital transformation dictates the pace of business innovation, DORA's upcoming regulations offer both challenges and opportunities for IT teams across the financial sector.
StackState stands at the forefront of this transformation, offering an exceptional observability platform that not only ensures compliance with DORA but also takes your IT operations to new levels of efficiency and reliability.
With StackState, IT teams can confidently handle the challenges of DORA, knowing full well that their IT infrastructure is not only compliant but also optimized for resilience and excellence.
We invite you to take a closer look into the world of full-stack observability by exploring the StackState playground and unlocking a new dimension of application management. Visit the StackState Playground now.