Once upon a time, in a tech company, an engineering team had the freedom to independently deploy updates and new features to a Kubernetes cluster. This autonomy helped speed up development but also led to unforeseen issues with resource management.
The platform team responsible for maintaining the cluster's health noticed an increase in orphaned Persistent Volumes (PV), a piece of plug-in storage independent of other Kubernetes cluster pods. Left behind after the associated pods were deleted, these PVs were not only using valuable storage space, they were also increasing operational costs and potential security risks.
This situation underscored the need to improve tracking and resource lifecycle management within the cluster, leading to a more structured approach to ensure resources were efficiently addressed and cleaned up post-deployment.
This article is divided into six sections to guide you through the best practices for handling orphaned resources in Kubernetes, including:
What orphaned resources are and why they occur in Kubernetes environments.
Examples of common orphaned resources typically found in Kubernetes such as Persistent Volumes, ConfigMaps, and Secrets.
The impact of orphaned resources and their negative effects on cluster performance, security, and cost efficiency.
Detecting orphaned resources with our step-by-step guide using K8s commands and best practices.
Preventing the accumulation of orphaned resources, which involves implementing lifecycle management strategies and leveraging Kubernetes' native features.
Using StackState for automated detection and management of orphaned resources with out-of-the-box monitoring to improve cluster maintenance and security.
What are orphaned resources in a Kubernetes cluster?
Orphaned resources in a Kubernetes cluster, including volumes, container images, ConfigMaps, and secrets, continue to consume system resources despite no longer being utilized by active applications. They typically result from factors like application updates, deletions, or configuration modifications, having become detached from functional components over time.
These orphaned items persist within the cluster, consuming storage, memory, and processing resources, which can result in inefficiencies. Since Kubernetes does not automatically clean them up, identifying and removing them manually is necessary to ensure optimal cluster health and performance.
Identifying and managing these wasted resources is important for avoiding security risks, compliance issues, and unnecessary cost overruns.
What are some examples of common orphaned resources?
In a Kubernetes cluster, various resource types commonly become orphaned, demanding careful management to prevent them from negatively affecting the cluster’s efficiency and security.
Persistent Volumes (PVs) are storage resources that often persist after the pods utilizing them have been deleted. Initially provisioned to store data across pod restarts and deployments, these volumes become redundant (and expensive to keep) when their associated pods are removed without cleaning up stored resources. But be careful; PVs typically store critical data from databases to customer information. They may frequently be orphaned during upgrade processes or when solely accessed in batch processing jobs. Therefore, verifying that the data within is no longer needed before deleting is crucial.
Container Images, another common orphaned resource, are cached within cluster nodes to accelerate future deployments. However, in environments with high deployment churn rates, old or unused images can accumulate and take up valuable disk space. When newer versions are deployed, these images become orphaned, and the older versions are no longer necessary but still occupy space on the node.
ConfigMaps and Secrets store configuration data and sensitive information needed by applications running in the cluster. They can become orphaned when the applications or services that referenced them are updated or deleted. Without proper tracking and cleanup, these objects remain in the cluster, potentially exposing sensitive information or simply consuming resources.
Network policies, defined to control the traffic flow between pods within a cluster, can also become orphaned. This typically occurs when the pods or namespaces they were designed to protect are deleted. The policies persist without serving any purpose, leading to unnecessary complexity and potential security loopholes.
Completed jobs or pods that have finished execution might not always be properly cleaned up. These can leave behind residual configurations or data, cluttering the cluster and, over time, leading to performance degradation.
What is the impact of having orphaned resources?
Having orphaned resources in a Kubernetes cluster can significantly impact the overall health of your infrastructure. These resources, while inactive, continue to consume various system resources, leading to the following issues:
Resource wastage: Resource Misuse: Orphaned resources, such as unused volumes, outdated container images, and inactive ConfigMaps, occupy valuable system resources like storage, memory, and CPU. This reduces the resources available for active applications and increases costs, especially in cloud environments where you pay for resources utilized.
Performance and stability issues: Excessive orphaned resources can clutter the system, resulting in decreased performance. For example, too many unused volumes can cause storage overprovisioning, while residual container images can fill up disk space, potentially causing node performance issues or failures. This resource clutter can slow down operations such as backups, scaling, and recovery, impacting the overall system stability.
Security risks: Orphaned resources, especially ConfigMaps and Secrets containing sensitive information, present security risks if not appropriately managed. If left unmonitored and unsecured, they can become unintended backdoors for data breaches.
Operational overhead: Manually tracking and cleaning up these resources can be time-consuming and prone to errors. This additional task distracts from more strategic activities and increases the risk of mistakes during cleanup, which could inadvertently affect active resources.
Compliance and governance: Orphaned resources can complicate compliance audits for organizations subject to regulatory requirements. Unused and unmanaged resources may not adhere to the compliance standards set for data handling and security, potentially resulting in violations and penalties.
How to detect orphaned resources
Detecting orphaned resources in a Kubernetes cluster involves a few systematic steps to ensure that all unused resources are identified and evaluated for cleanup.
Here are 4 steps to help you effectively detect and deal with orphaned resources:
List all resources in your cluster: Use our examples of common orphaned resources in this article as a starting point. You can use Kubernetes commands to list these resources. For example:
To list all ConfigMaps:
`kubectl get configmaps --all-namespaces`To list all Secrets:
`kubectl get secrets --all-namespaces`To list all Persistent Volumes (PVs):
`Kubectl get pv -o custom-columns='NAME:.metadata.name,STATUS:.status.phase'`where STATUS will be "Released" for orphaned volumesTo list all Persistent Volume Claims (PVCs):
`kubectl get pvc --all-namespaces`
Identify active resources used by pods or deployments: You can check the usage of ConfigMaps and Secrets by querying the pods that reference them:
To check which pods are using a ConfigMap:
`kubectl get pods --all-namespaces -o=jsonpath="{.items[?(@.spec.containers[*].envFrom[*].configMapRef.name=='CONFIGMAP_NAME')]}"`Check which pods are using a Secret:
`kubectl get pods --all-namespaces -o=jsonpath="{.items[?(@.spec.containers[*].env[*].valueFrom.secretKeyRef.name=='SECRET_NAME')]}"`
Compare lists of all resources with those currently in use: Any resource not referenced by any active workload is considered orphaned. This can be done manually or through scripts that automate the comparison.
Review orphaned resources before deletion: Some might appear unused but could be part of a failover strategy, temporarily idle, or scheduled for future use.
How to prevent orphaned resources
Preventing orphaned resources in a Kubernetes cluster involves proactive management. Implementing these strategies can significantly reduce the occurrence of orphaned resources, leading to a more efficient and cost-effective Kubernetes environment.
Here are three concrete strategies to minimize the risk of resources becoming orphaned:
Implement ownership and labels: Use Kubernetes' built-in ownership and label mechanisms to keep track of resource relationships and dependencies. By defining clear ownership through labels and annotations, you can ensure that when a primary resource is deleted, all associated resources are automatically identified for cleanup. For example, setting owner references on ConfigMaps and Secrets linked to a specific deployment kicks off automatic cleanup when the deployment is deleted. This promotes efficient management of resources and reduces the risk of orphaned items.
Regular audits and monitoring: Routine checks of your Kubernetes resources will help detect and resolve orphaned resources before they accumulate. Use monitoring tools designed to track resource usage over time and alert you to any that have not been accessed or used within a set period.
Integrate cleanup into CI/CD pipelines: As environments are spun down or applications are updated, automate the deletion of associated resources. This ensures that every deployment cleanup leaves no unused resources behind.
How to use StackState to continuously detect orphaned resources
StackState provides a powerful out-of-the-box monitor specifically designed to continuously detect orphaned resources within a Kubernetes cluster. This feature is particularly valuable as it requires no additional configuration from your dev teams.
Once deployed, it automatically monitors the cluster for any resources that are no longer in use but still consuming system resources. Operating seamlessly in the background, it ensures that all teams deploying to the cluster can effortlessly detect and report on orphaned resources.
This proactive monitoring helps maintain cluster efficiency, reduces costs by eliminating wasted objects, and enhances security by preventing potential vulnerabilities associated with unused and unmonitored resources.
Once an orphaned resource is detected, StackState’s remediation guides provide a clear, step-by-step explanation of how to resolve and overcome this issue. With this feature, you don’t have to be an expert to effectively manage your resources and maintain a clean cluster.
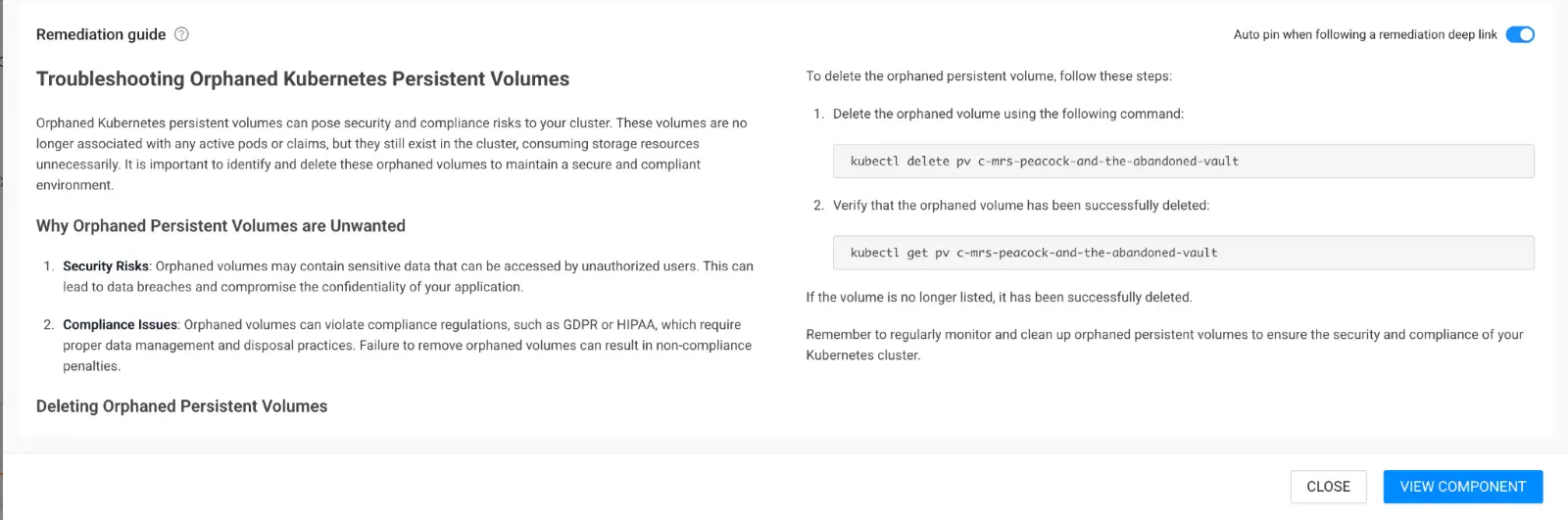
StackState delivers significant value by automating a crucial maintenance task related to optimizing and securing the Kubernetes environment. Platform teams, in particular, who are most often tasked with this responsibility, now have an easy way to control K8s resources.
Want to see it for yourself? StackState offers access to a live demo environment where you can observe the orphaned resources monitor in action and explore its capabilities firsthand.
Further reading: